Outsmart Cybercrime: How Real-Time Monitoring Enables Proactive Security

Cybercrime has been increasing, with the number of attacks per year increasing and the monetary losses associated with it. Securing systems and sensitive data is more important than ever.
Understanding Cybercrime
Cybercrime encompasses criminal activities targeting or utilising computers, networks, or digital devices to illicitly gain financial profit, political advantage, personal satisfaction, or to cause harm. These attacks can manifest in various forms, including phishing, malware, ransomware, data breaches, distributed denial of service (DDoS), SQL injection, and social engineering. The repercussions of cybercrime are far-reaching, resulting in substantial financial losses, compromised personal and sensitive information, and damage to individual and organisational reputations.
The Importance of Proactive Security
In the ever-evolving landscape of cyber threats, organisations face a critical choice: react or prevent. A reactive approach involves responding to security incidents after they occur, such as data breaches or system failures. While essential for damage control, it’s often a costly and time-consuming process.
On the other hand, a proactive cybersecurity strategy focuses on preventing attacks before they happen. By anticipating potential threats, organisations can implement safeguards, strengthen defences, and minimise vulnerabilities. This forward-thinking approach is increasingly crucial as cybercriminals become more sophisticated.
A proactive stance offers numerous advantages. It not only prevents financial losses but also safeguards your organisation’s reputation. By detecting threats early, you can respond swiftly and effectively, reducing downtime and minimising the impact of a potential breach.
Ultimately, a balanced approach that combines both reactive and proactive measures is ideal. While a robust incident response plan is essential, investing in prevention is the most effective way to protect your organization from the growing cyber threat landscape.
What is Real-Time Monitoring?
Real-time monitoring is the art of capturing, processing, and responding to data as it happens. It’s the pulse of your operation, delivering a constant stream of information that empowers you to make split-second decisions. Imagine having a crystal ball that reveals the present, not just predicts the future. That’s the power of real-time monitoring.
Security Information and Event Management (SIEM) systems are a critical component of real-time monitoring, especially in cybersecurity. By aggregating and analyzing security data from various sources, SIEM helps organizations detect threats, investigate incidents, and respond effectively.
In today’s fast-paced world, real-time monitoring is no longer a luxury but a necessity. By harnessing the power of real-time data, businesses can gain a competitive edge, improve efficiency, and mitigate risks.
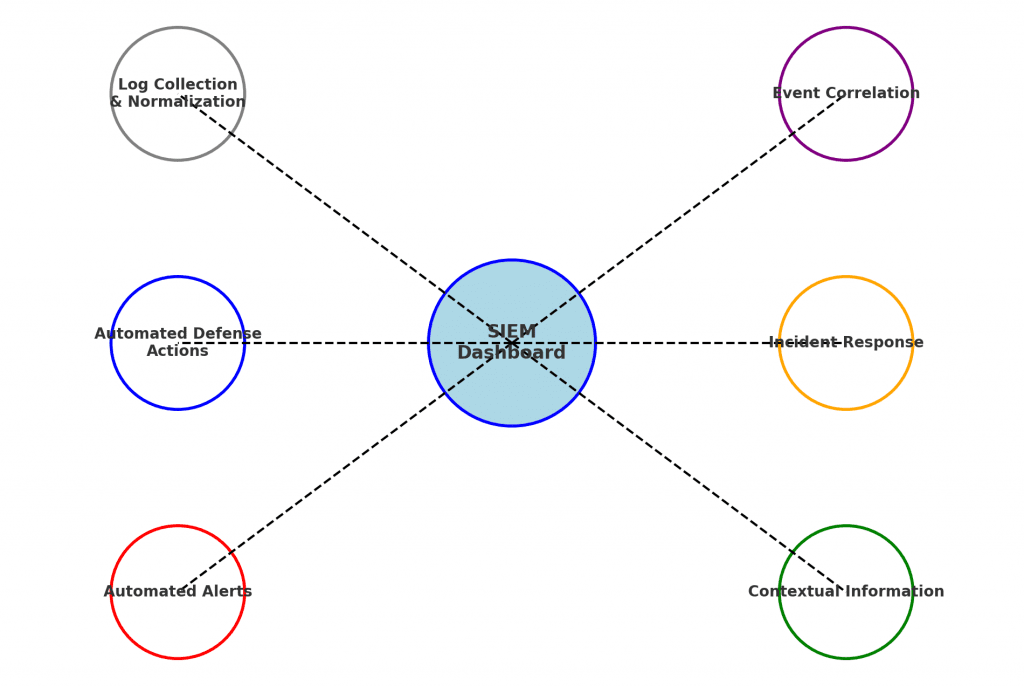
Benefits of using a SIEM solution

A SIEM solution offers significant advantages for real-time monitoring by centralising and normalising log data from diverse sources. This enables the swift detection of threats through the correlation of events. Key benefits include:
- Automated Alerts: Immediate notifications of potential security incidents.
- Contextual Information: Enhanced incident response with detailed, contextual data.
- Automated Defence Actions: Proactive security measures to mitigate threats.
Additionally, SIEM tools enhance compliance monitoring and reporting, facilitate anomaly detection through behavioral analytics and machine learning, and offer real-time dashboards for visual insights. These capabilities collectively improve an organisation’s security posture by allowing for timely threat detection and efficient response, ultimately reducing the risk of security breaches.
There’s a whole ecosystem of data processing tools out there, including big names like Opensearch, Elasticsearch, and Splunk. These platforms are incredibly powerful, but they often require a deep dive into complex configurations and coding. This can be a major hurdle for teams without dedicated data engineers.
That’s where Predictive PremOS shines. We’ve taken the best aspects of these open-source tools and built a user-friendly interface that simplifies the entire process. With Predictive PremOS, you don’t need to be a data scientist to extract valuable insights from your data. It’s designed to be intuitive, allowing you to focus on making informed decisions rather than wrestling with complex software.
Conclusion
SIEM solutions undoubtedly serve as a cornerstone in the modern security architecture, offering real-time visibility into network activities, enabling rapid threat detection, and facilitating efficient incident response. However, the complex and ever-evolving nature of cyber threats necessitates a holistic approach that extends beyond SIEM capabilities.
To truly safeguard an organisation, a multi-layered strategy encompassing various security controls, technologies, and human processes is essential. This includes, but is not limited to, endpoint protection, network security, identity and access management, data loss prevention, and security awareness training. By combining the strengths of SIEM with these complementary measures, organisations can create a robust security posture that effectively mitigates risks and protects critical assets.
In our next blog, we will explore the concept of holistic security in greater detail, discussing the key components of a comprehensive security framework and providing actionable recommendations for implementation.
Related Posts


