A World Class Immune System For Your IoT Infrastructure
Secure IoT Platform
Software and Hardware LoRa Gateway for ARM and Intel Platforms with built-in AI.
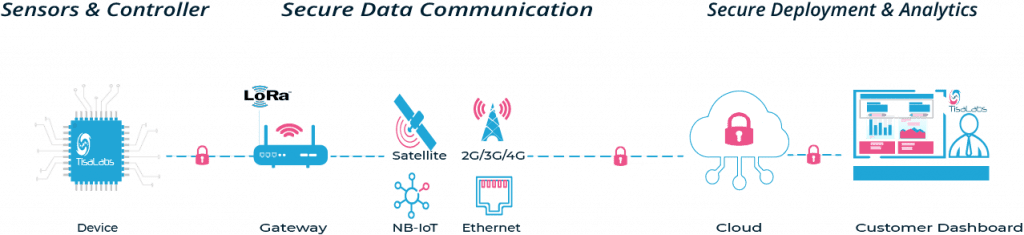
End-to-end secure ioT platform
Introducing our Secure IoT Platform—an innovative solution designed to revolutionize the way you manage and harness the power of your IoT ecosystem. This platform provides a comprehensive view into your end devices and gateways, offering customizable dashboards and widgets for a tailored and insightful experience.
With a focus on security, our Secure IoT Platform ensures the integrity and safety of your connected devices, allowing you to explore the full potential of your IoT network without compromising on safety. From real-time monitoring to historical data analysis, our platform empowers you to extract actionable intelligence, enabling informed decision-making.
Experience a new standard of efficiency and innovation with our Secure IoT Platform, where visibility, security, and customization converge to redefine the possibilities of your connected world.
Benefits
Secure Field Deployment
improve your IoT experience with our state-of-the-art OTA update system. Enjoy the peace of mind that comes with our compatibility verification feature, allowing you to thoroughly assess updates before deployment. Seamlessly transition your devices with intelligent updates that optimize the process, ensuring a smooth and efficient upgrade without any disruption to your hardware's functionality. With dynamic delivery, you hold the power to push live OTA updates in just 30 seconds, eliminating the anxiety of bricking your devices. What's more, our system guarantees a thorough verification of software and firmware security before deployment, enhancing the overall reliability of your IoT ecosystem. Upgrade confidently, stay ahead of the curve, and unlock the full potential of your IoT devices with our innovative OTA update solutions.
Unified Device Management
revolutionise Hardware and Software management by providing a single, unified interface for all your devices. This streamlined approach simplifies the complexities associated with overseeing diverse hardware components, offering a centralized dashboard for efficient monitoring. Users benefit from an enhanced and consistent experience, navigating seamlessly across various devices without the need for multiple applications. Beyond user convenience, this unified interface translates into tangible time and cost savings, as teams can perform tasks and implement changes more efficiently. Moreover, it contributes to improved decision-making by presenting comprehensive data in a cohesive manner. The platform's commitment to compatibility and integration ensures smooth operations, facilitating the seamless incorporation of new devices and fostering scalability within your IoT ecosystem.
Unified Cross-Device Data Access
We prioritize device agnosticism, ensuring seamless integration with a diverse range of IoT devices, from sensors to actuators. This universal accessibility extends beyond geographical boundaries, allowing you to retrieve real-time insights and monitor device performance from anywhere in the world. Enjoy cross-device compatibility, whether you're using smartphones, tablets, laptops, or desktop computers. This approach breaks down device silos, providing a unified interface for data retrieval. The result? Enhanced decision-making capabilities and increased operational efficiency, making our platform a catalyst for success in your dynamic IoT environment.
Key Features
Converged Communications
Tailored for large-scale deployments in diverse environments, from vast agriculture fields to robust industrial facilities, this solution provides unparalleled flexibility. With robust support for Satellite, cellular, WiFi, and Ethernet, our converged communications feature ensures a versatile and reliable connectivity experience.

Builtin AI Processing
Artificial Intelligence (AI) processing at the edge of the network, allowing for real-time analysis and decision-making directly within the gateway. This reduces latency and enhances the overall responsiveness of your IoT system.
Predictive Analytics
Harness the power of AI-driven predictive analytics to foresee potential issues and anomalies in the data collected by your IoT devices. This proactive approach enables predictive maintenance and helps prevent critical failures.
Deployment at Scale
Optimize power consumption through AI algorithms that intelligently manage device communications. By understanding usage patterns, the gateway can conserve energy during periods of inactivity, extending the life of battery-powered devices.

Security Enhancement
AI-driven security measures to detect and respond to potential threats in real-time. This includes anomaly detection, intrusion prevention, and the ability to adapt security protocols based on evolving attack patterns.
Autonomous Decision-Making
Leveraging LoRa communication, this autonomy becomes especially invaluable in scenarios demanding swift responses, such as within smart agriculture applications encountering abrupt shifts in weather conditions.
Tamper proof digital identity
Crafted with precision and fortified with advanced encryption, our keys create an impenetrable shield around your digital identity. By seamlessly integrating into your authentication process, these keys ensure that only authorised individuals gain access, thwarting any attempts at unauthorised entry. With the reliability of ironclad security, you can trust our hardware keys to safeguard your identity in an ever-evolving digital landscape.

Vulnerability Assessment
Enhance your security with our advanced vulnerability assessment. We meticulously check for vulnerabilities in source code, binaries, Kubernetes deployments, and Docker images before deployment. This proactive approach ensures robust protection for your ecosystem, providing peace of mind against evolving cybersecurity challenges."
Use Cases
Smart Agriculture
With the growing adoption of the Internet of Things (IoT), connected devices have penetrated every aspect of our life. The Tisa-GW device allows you to collect Data from sensors located on the whole farm spanning over multiple kilometers. The Devices are able to transmit the data to the Tisa-GW gateway using LoRa communication technology making it possible to sense a large number of areas.
Smart Transportation
Smart Transportation and smart city traffic management are revolutionising how cities approach mobility and emergency response, while reducing congestion on city streets. The Tisa-GW device offers critical information related to locations, weather analytics, and more. Fleet managers can also track fuel economy and monitor routine expenses like gas and repairs.
Smart Manufacturing
Organizations aim at a better understanding and usage of Industrial Internet of Things (IIoT) data. In general, data generated by IIoT devices can provide companies with deep insights enabling them to build products faster and more effectively. The Tisa-GW Gateway combined with the cloud management platform was built to server increasing demands from global digitalization of manufacturing in a variety of fields requiring Realtime data to make better decisions thus saving time and many to be more competitive.
Any questions?
We’re here to help
Check out these common questions and answers or read more by clicking Knowledge Base. If you don’t find what you need, check our Support Team for assistance.
What is IoT security?
IoT security refers to the measures and practices in place to protect the Internet of Things (IoT) devices and systems from potential cybersecurity threats and vulnerabilities. It encompasses a range of technologies and processes designed to safeguard IoT devices, data, and networks from unauthorized access, data breaches, and other security risks.
Why is IoT security important?
IoT security is crucial because IoT devices are often connected to the internet and collect sensitive data. If these devices are not adequately secured, they can become entry points for cyberattacks, putting data privacy, infrastructure, and public safety at risk. Robust IoT security is essential to prevent unauthorized access, data breaches, and system disruptions.
What are common IoT security challenges?
Common IoT security challenges include weak or default device passwords, lack of regular firmware updates, insufficient encryption, and vulnerabilities in IoT device hardware or software. Managing a large number of diverse IoT devices and ensuring they remain secure throughout their lifecycle is also a significant challenge.
How can IoT security be improved?
IoT security can be improved through various means, such as implementing strong device authentication, encryption, and access controls. Regularly updating device firmware to patch known vulnerabilities, monitoring network traffic for anomalies, and educating users on best security practices are also important steps in enhancing IoT security. Collaboration between device manufacturers, service providers, and security experts is essential to address emerging threats and vulnerabilities effectively.
